- HubPages»
- Technology»
- Internet & the Web»
- Web Page & Web Site Development
10 Wordpress Security Measures That You Can't Miss!

Wordpress is one of the most used content management systems around today -- it is also one of the most targeted, by hackers. Anyone running a self-hosted Wordpress site has to be ready to defend it when something goes wrong.
This guide gives you the top 10 most fundamental tips in securing your Wordpress-powered website. All of these measures can be performed either before or after installation!
#10...
Beware of CHMOD 777
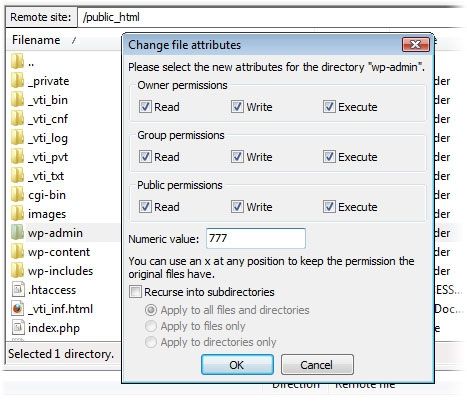
When you CHMOD your Wordpress files, be sure you know what you're doing, and what changes you've made. The most dangerous CHMOD code is 777, which gives all groups and users full read, write and execute permissions to a folder or file. This is the level of access that hackers would need in order to inflict a lot of damage on your site, depending on what it's applied to.
Many folders need to be write-able (755) in Wordpress in order for certain things to function. Just be wary of assigning a 777 to anything. For a more technical look at Wordpress CHMOD defaults and security recommendations, see this section of the Changing File Permissions page.
Using your FTP software, browse all of your categories and make sure nothing is set to 777, as it is completely unnecessary for anything to be set to this.
#9...
Use Robots.txt to Moderate Access
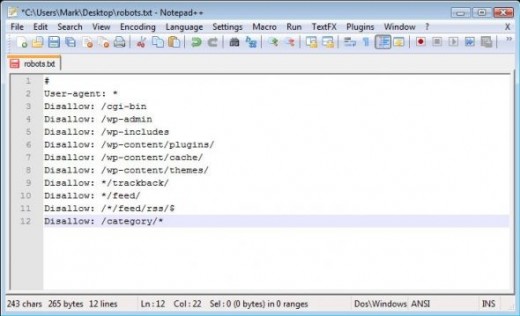
Your site's robots.txt file is used to tell search engines which folders of your site they should not look into for indexing purposes. You'll want to tell them not to look into folders that are unnecessary for them, such as the "/plugins" and "/wp-admin" folders.
Simply copy and paste the code below into a Notepad document, and save it as "robots.txt", then add it to the root directory of your Wordpress site:
#
User-agent: *
Disallow: /cgi-bin
Disallow: /wp-admin
Disallow: /wp-includes
Disallow: /wp-content/plugins/
Disallow: /wp-content/cache/
Disallow: /wp-content/themes/
Disallow: */trackback/
Disallow: */feed/
Disallow: /*/feed/rss/$
Disallow: /category/*
By default, there is no reason for search engines to be looking into any of these folders! Be sure to customize this list by adding any other folders that you wish to be hidden from search engine results, too. This is a completely legitimate process that is endorsed by Google, Bing and others.
#8...
Remove All "Wordpress" References
Nobody needs to know that it's Wordpress! Never include any reference, such as "Powered By Wordpress," or your version number. While we all love WP, hackers that are looking to target Wordpress sites might do a search for phrases like this, just so that they can find their next target.
#7...

Drop A Blank HTML File Into Your Folders
This is the oldest trick in the book. Open up Notepad. Don't type anything in, and just save the blank page as "index.html." Then, simply save this file into each directory, such as ..wp-content/plugins (new versions of Wordpress SHOULD already have one in there, that says "Silence Is Golden" within it).
By doing so, you're preventing anyone from seeing a list of files in your site folders by giving them a blank white screen to look at! Exploiting Wordpress sites with outdated plugins is one of the most common attacks, and this will help mask some information.
#6...
Be Fully Upgraded At All Times - Being up-to-date = being secure
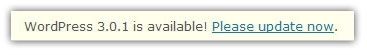
Sorry to repeat the same thing you've already gotten drilled into your head - but by having the most recent version of Wordpress and all of its plugins, you'll make a huge stride toward having a secure site.
Vulnerabilities are always exploited by hackers. When a new version of Wordpress is out, it will notify you at the top of your admin panel. Now that Wordpress has its own auto-upgrade function, it's easier than ever.
Check your plugins list frequently, and upgrade any of them when you're prompted about a new version.
#5...
Change your Default Wordpress Database Prefix
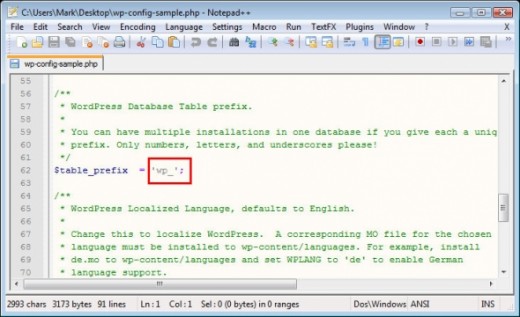
When installing Wordpress, you'll have the option of using the default "wp_" as your table prefix (i.e., wp_comments, wp_links, wp_posts, etc.) You can change this to something else if you'd like - it's another measure toward straying away from default attributes.
It's easy. Just open wp-config-sample.php, find the prefix area as seen in the screenshot, and change "wp_" to something else, like "me_" or "cool_" or whatever you want. It's yet another measure that makes things very difficult on hackers. Don't forget, this file will have to be renamed to "wp-config.php" before you install Wordpress.
#4...
Use .htaccess to Protect Wordpress
Your .htaccess file will allow you to input commands that search engines will follow the instant they start to load your site. Add this code at the beginning of your .htaccess file to protect Wordpress from script injections:
Options +FollowSymLinks
RewriteEngine On
RewriteCond %{QUERY_STRING} (\<|%3C).*script.*(\>|%3E) [NC,OR]
RewriteCond %{QUERY_STRING} GLOBALS(=|\[|\%[0-9A-Z]{0,2}) [OR]
RewriteCond %{QUERY_STRING} _REQUEST(=|\[|\%[0-9A-Z]{0,2})
RewriteRule ^(.*)$ index.php [F,L]
Add this at the end of the .htaccess file to protect "wp-config.php" from bad bots:
order allow,deny
deny from all
This line will disallow anyone from seeing a directory tree of your sub-folders:
Options -Indexes
#3...
Create A Separate .htaccess File for WP-Admin
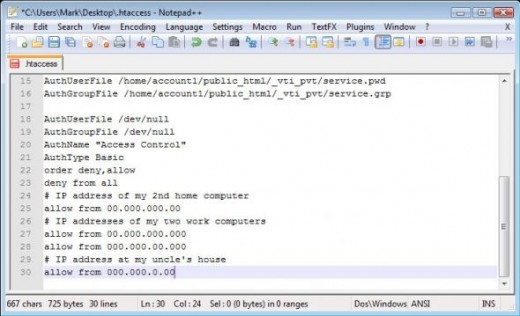
I've learned this one from an article written by Google engineer Matt Cuts. By creating an .htaccess file just for your WP-Admin folder (not to be confused with your main .htaccess in the root directory), you can block all IP addresses except the ones you specify.
Here's what the contents of this file should look like (just open up Notepad, and copy & paste this in...then, replace the dummy IP's with the ones from your other home or work computers):
AuthUserFile /dev/null
AuthGroupFile /dev/null
AuthName "Access Control"
AuthType Basic
order deny,allow
deny from all
# IP address of my 2nd home computer
allow from 00.000.000.00# IP addresses of my two work computers
allow from 00.000.000.000
allow from 000.000.00.000# IP address at my parent's house
allow from 000.000.0.00
#2...
Password Protect WP-Admin on the Server Side
Here's a second brick wall that hackers would have to get through. This will be a minor annoyance to you, but a great additional barrier for the security of your site!
On your web server, get into your Wordpress site's account. Find the option for "Password Protect Directories" (this is what it's called in cPanel, but it might be named differently on another platform). Password protect the directory "wp-admin." Give it a unique password, and write it down.
Now, if someone attempts to visit YourSite.com/wp-admin, they'll get nothing but a white screen and a pop-up box from the server, asking for a username and password. Unless they know of these, they'll never be able to see the Wordpress admin log-in screen.
Of course, this will now give you two passwords you'll have to enter in order to edit your site (the server password and the Wordpress admin password), but you can have your browser "remember" all of these so that you don't have to type them in every time. Just don't lose the passwords!
#1...
Rename "Admin" to Something Else

When you first create a Wordpress site or blog, the default login that most people create is a default account called "admin." Be sure NOT to do this, since it's not mandatory to name your admin account "admin." Instead, use a different name as your administrator login.
If you use "admin," you're using the most common login that hackers will attempt to get in with, and you'll make the job 50% easier on them if you do! If you've already named your account "admin," simply go into your "users" menu, create a new user and give it administration rights, then remove the default account.
More Wordpress Security Measures - Further tweaks to secure your Wordpress installation
- Hardening Wordpress
It's a Wordpress security tutorial written BY Wordpress! A must-read.